Log Info Disclosure on droids0 Android App
In this writeup, I will walk you through the steps I took to solve the droids0 challenge from PicoCTF 2019, which involves Android reverse engineering. This challenge requires analyzing an APK file to uncover a hidden flag. I will detail the tools and methods used to extract the flag, including decompiling the APK, examining the code, and using Logcat to capture the output. Let’s dive in.
Tools that I used:
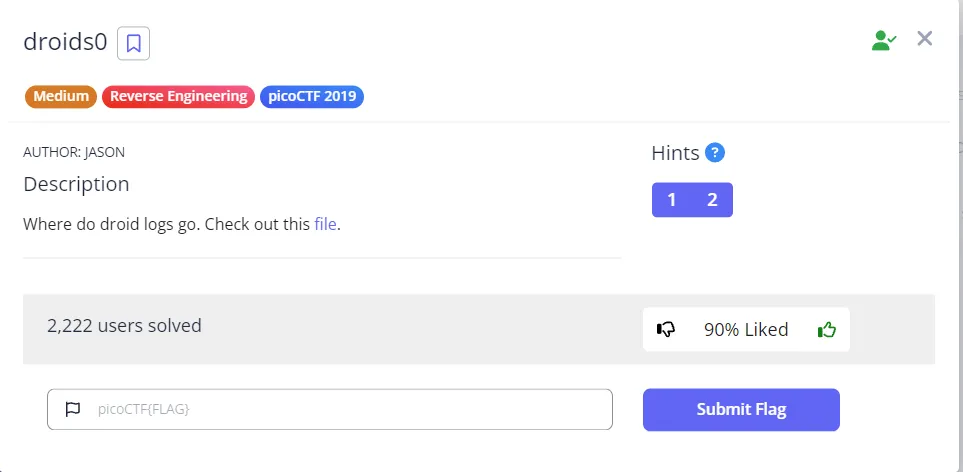
After downloading the APK, it gives me this screen. There are 2 TextViews, 1 EditText, and 1 Button. I assume we need to submit some “secret” into the EditText, then the flag will be shown.
When clicking the button, it shows “Not Today..” and there is a hint at the top: “where else can output go? [PICO]”
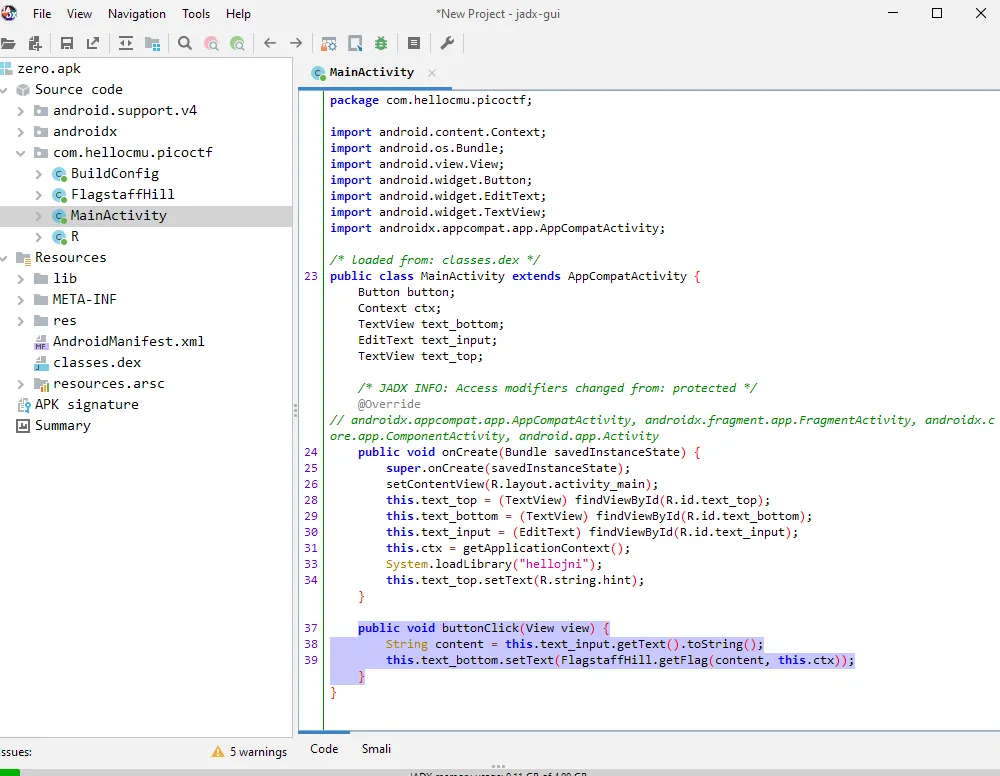
The first page I check is MainActivity since it usually handles the first page of an Android app.
In MainActivity, I found the function that handles the button click event. This function calls the getFlag() function in the FlagstaffHill() class.
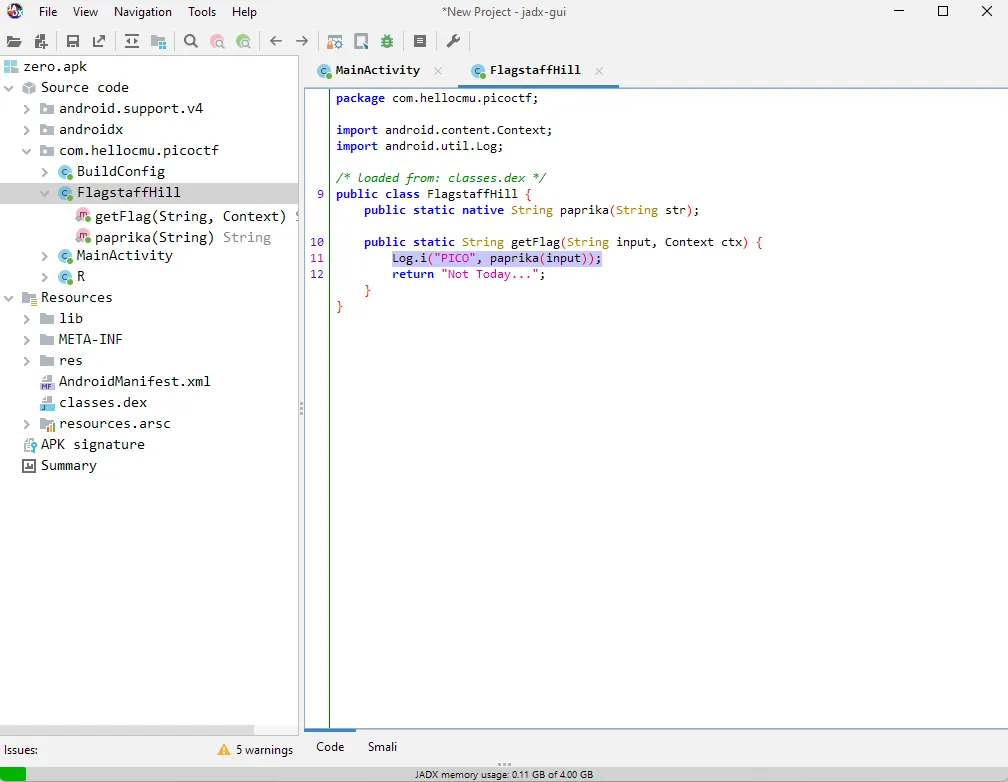
Then on the FlagstafHill class, it always returns “Not Today…” and there is a Log with the tag PICO and the value paprika(input).
The hint starts to make sense. Besides showing the output on the app, the developer can also show the output on Logcat.
Next, access the device shell via the terminal and check the Logcat.
adb shell
logcat
To make it easier to find, I spam-click the button so the log gets recorded multiple times.
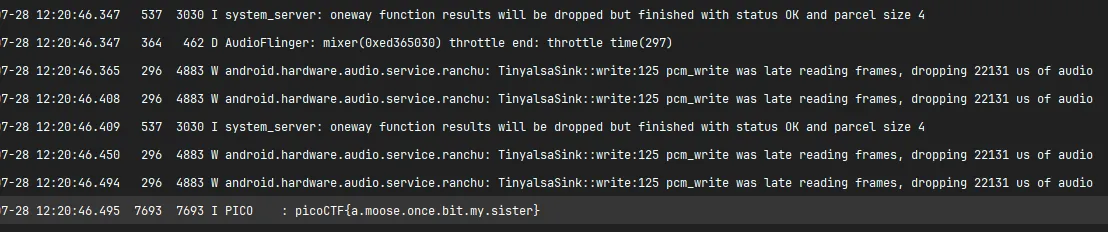
and then here’s the flag
picoCTF{a.moose.once.bit.my.sister}
Reference:
