Exposed Secret in Strings.xml on droids1 Android App
In this writeup, I will walk you through the steps I took to solve the droids1 challenge from PicoCTF 2019, which involves Android reverse engineering. This challenge is similar to droids0 but has a little different step for showing the flag.
Tools that I used:
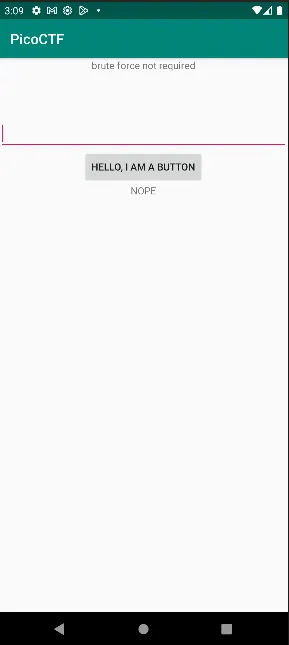
After downloading the APK, it gives me this screen. Similar to droids0 There are 2 TextViews, 1 EditText, and 1 Button. but this time the hint is “brute force not required” and the TextView on the bottom shows “NOPE” when the button is clicked.
for starter let’s send the APK to JADX and check the MainActivity
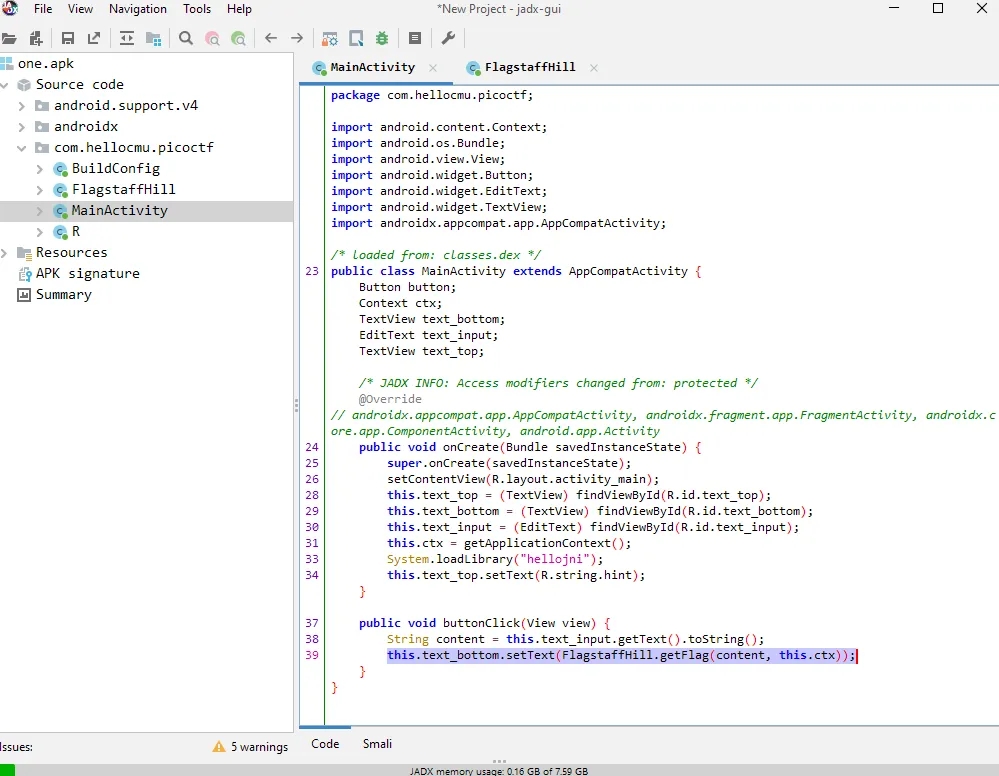
turns out the code on MainActivity is same with previous challenges (droids0) still use FlagstafHill.getFlag() function to show the flag so let’s just move to the FlagstaffHill Class
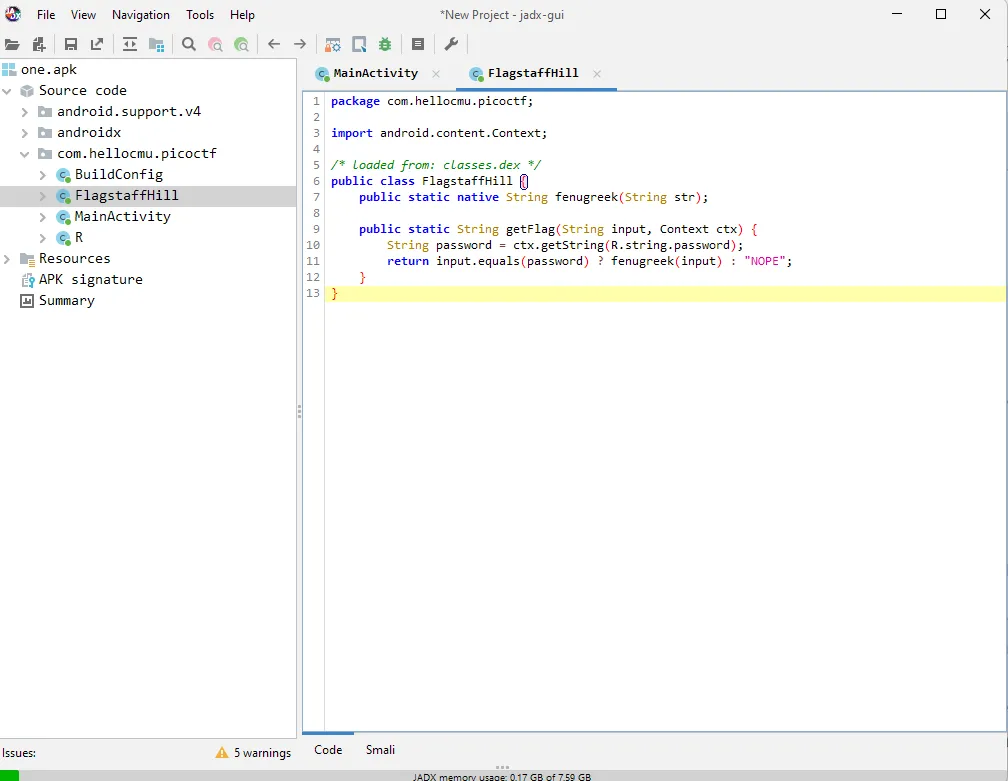
Okay, this time the code they don’t forget to return the flag like the previous challenge so let’s break down the code.
String password = ctx.getString(R.string.password);
this code means to create a string variable called password and the value is taken from Android strings resource with name “password”.
return input.equals(password) ? fenugreek(input) : "NOPE";
and this code checks if the input (from EditText) has same value as variable password then call fenugreek(input) and if it’s not the same then returns “NOPE”
it means that as long as we can get the “password” then it should return the flag, and according to the code when initializing the password variable, they get the password from the string resource. since on Android string resource is saved on strings.xml I can just jump into that file.
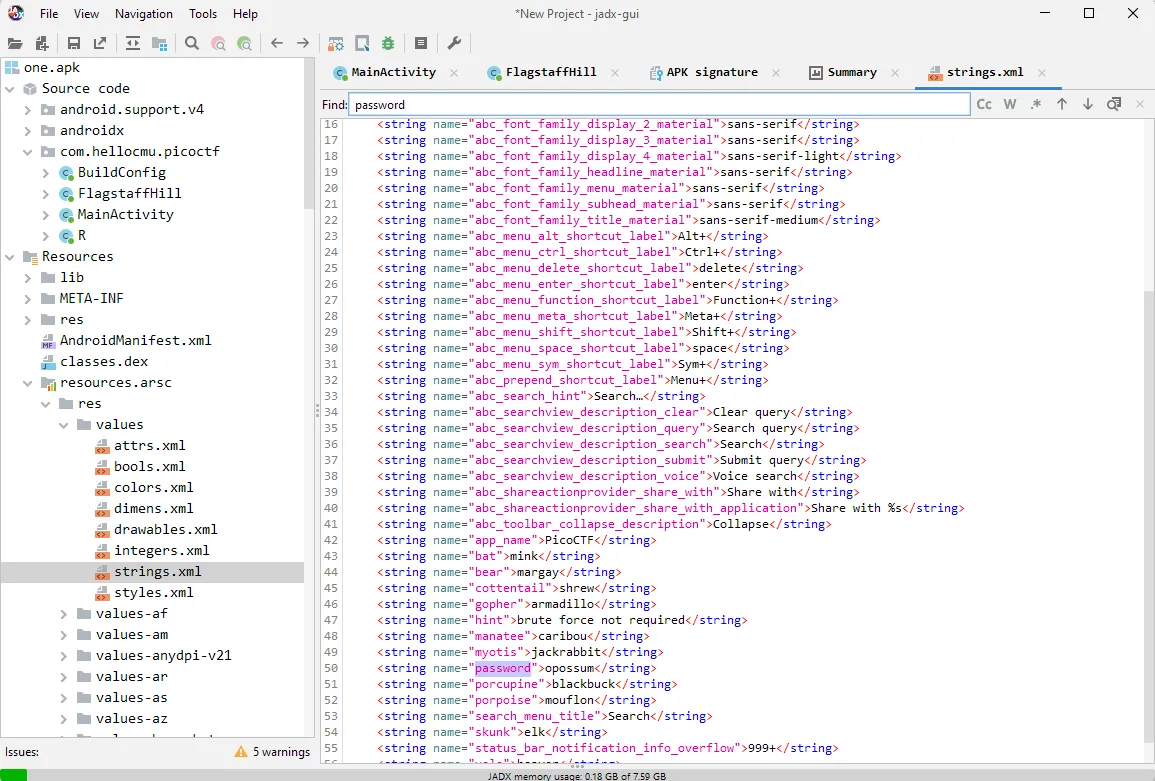
on strings.xml I found a string with the name password and value opossum, by this because I already found what the password is I just need to go back to the emulator and submit the password.
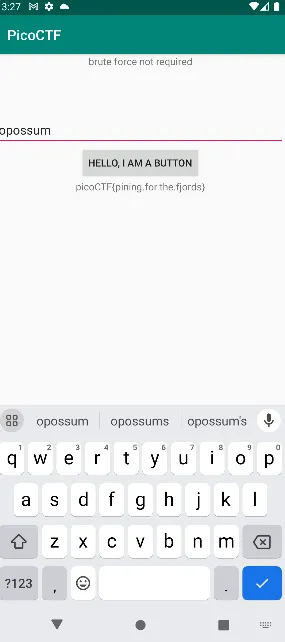
and here is the result, the flag is
picoCTF{pinning.for.the.fjords}
Reference:
