Malware Analysis with Event Viewer - PicoCTF 2025
Scenario
One of the employees at your company has their computer infected by malware! Turns out every time they try to switch on the computer, it shuts down right after they log in. The story given by the employee is as follows:
- They installed software using an installer they downloaded online
- They ran the installed software but it seemed to do nothing
- Now every time they bootup and login to their computer, a black command prompt screen quickly opens and closes and their computer shuts down instantly.
See if you can find evidence for the each of these events and retrieve the flag (split into 3 pieces) from the correct logs!
Story 1 They installed software using an installer they downloaded online
After Downloading the .evtx file, I opened it using built-in Event Viewer from Windows, after opened it turns out the Log contained large number of records. So i apply filter to make it easier to analyze.
The first step I focused on story 1 “the employee install software they download online”, to check this I apply filter for Event ID
- 1033: Software Installed
- 1040: Installation Started
- 11707: Installation Success
- 11724: Software Installation
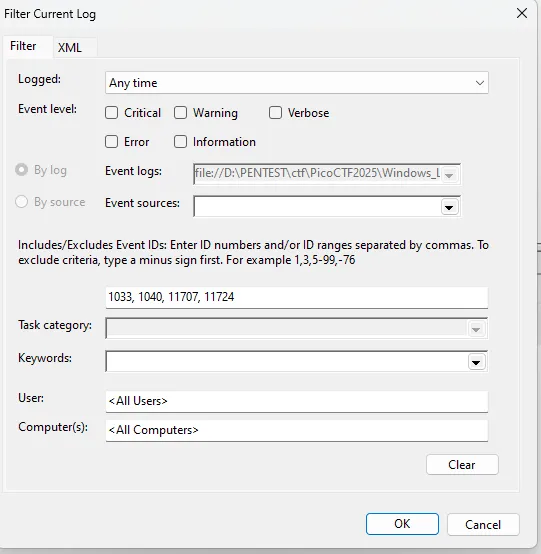
By applying this filter, the events record decreased to only 39, then I search manually 1 by 1 until 1 found this
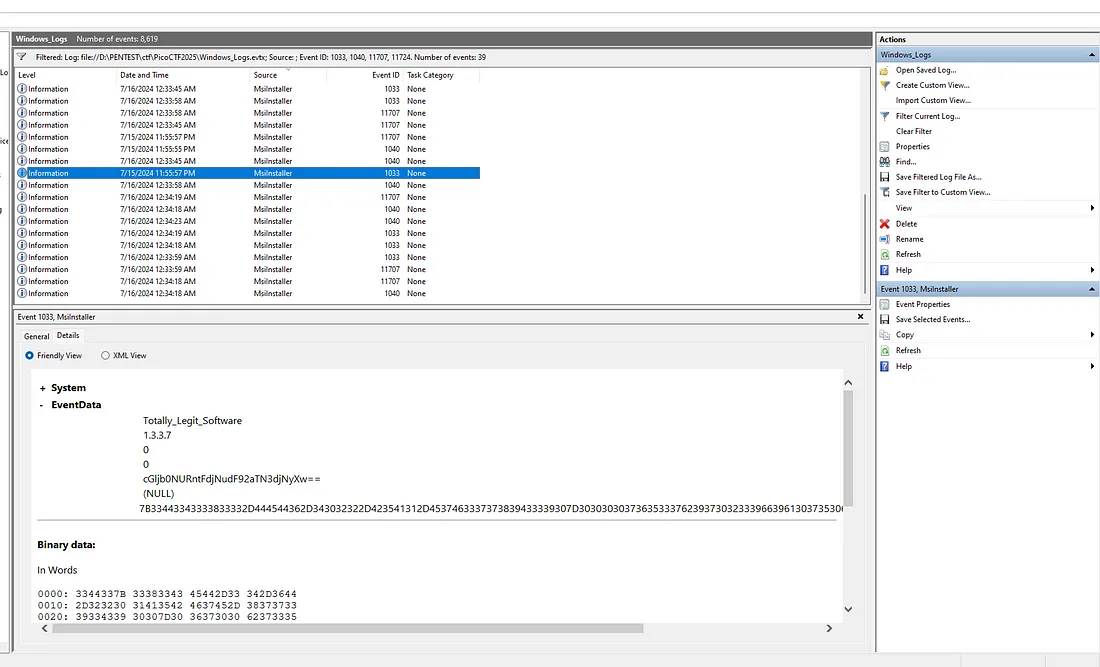
There is a Software Installation from “Totally_Legit_Software” and it contains a base64 encoded String
cGljb0NURntFdjNudF92aTN3djNyXw==
which, after decoding it using Cyberchef, the result is
picoCTF{Ev3nt_vi3wv3r_
Story 3 Now every time they bootup and login to their computer, command prompt screen quickly opens and closes and their computer shuts down instantly.
after finding first flag I jump to analyze Story 3 since the event quite straight forward and should be easier to find “every time user login, command prompt quickly open and close, then the computer shutdown”
to find this I just need to apply filter for event ID
- 1074: System has been Shutdown by process/user
and also adding timeframe that I got from Story 1, since the malware downloaded at 7/15/2024 11:55:57 PM. I put the time for events only after that
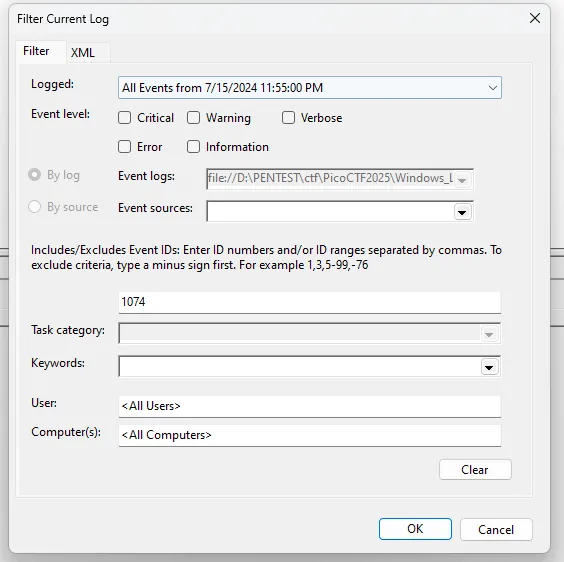
from this I got another flag part
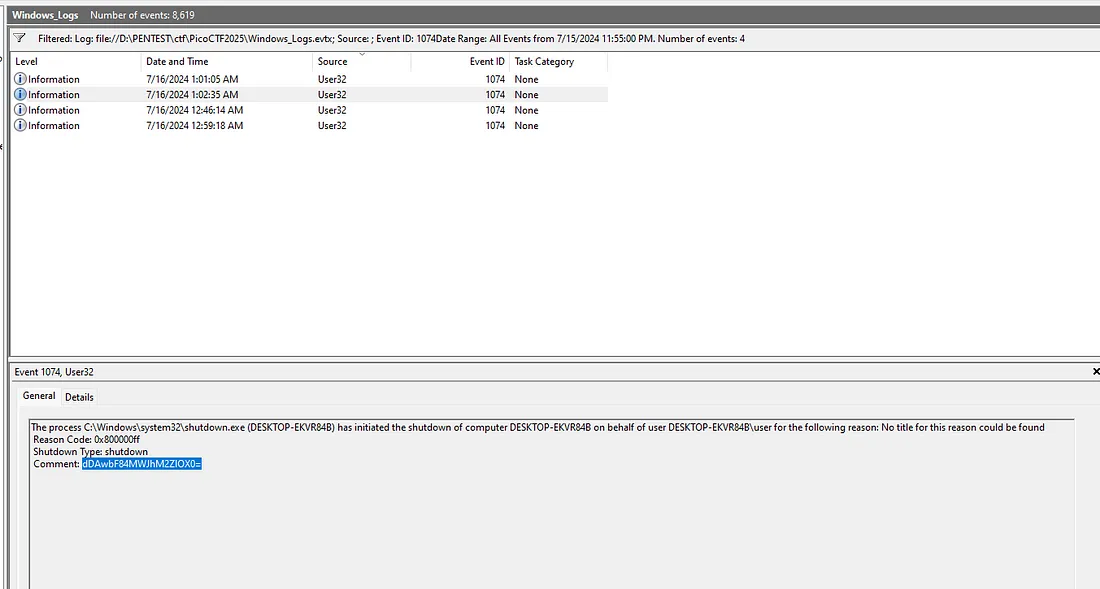
another base64 String
dDAwbF84MWJhM2ZlOX0=
which translate
t00l_81ba3fe9}
2. They ran the installed software but it seemed to do nothing
after finding the last flag part I go back to Story 2 “The software installed but it seemed to do nothing”
There are several possibilities that I think might happen during Story 2, like the malware run process on the background, or downloading some payload.
Since there is several possibilities and might take lot’s of Event ID to analyze I tried to apply this filter from what we already have
- The malware downloaded at 7/15/2024 11:55:57 PM & named “Totally_Legit_Software” on Event ID 1033 (Story 1)
- The Computer keep shutdown after login at 7/16/2024 1:02:35 AM on Event ID 1074 (Story 3) by having this, I apply filter to search All event ID except 1074 and 1033 also time from the malware downloaded until the computer shutdown.
after that I search “Totally_Legit_Software” using Find in Action Tab then I found this
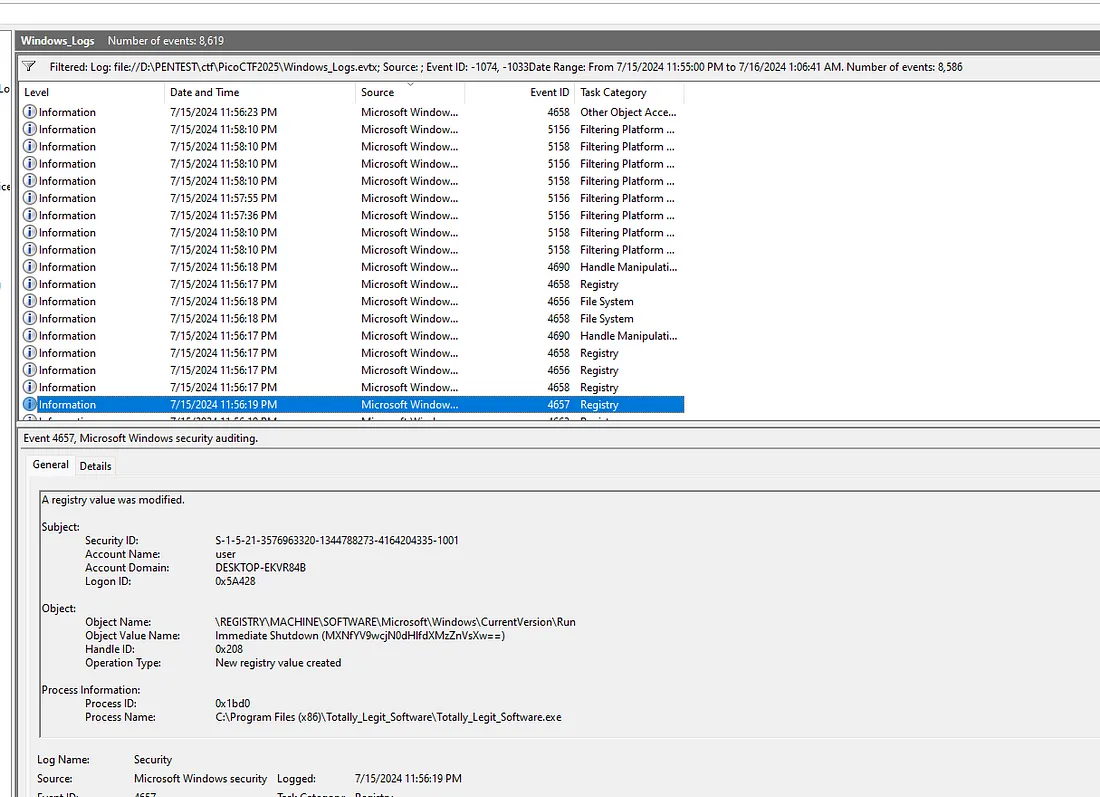
turn out on Story 2 the reason why the software not doing anything is because it modify Registry to for adding Immediate Shutdown when windows booted. Also on this Log I found another base64 String
MXNfYV9wcjN0dHlfdXMzZnVsXw==
which translate
1s_a_pr3tty_us3ful_
now all the flag part is found and by combining it I got
picoCTF{Ev3nt_vi3wv3r_1s_a_pr3tty_us3ful_t00l_81ba3fe9}
Reference:
