Weak Code Protection for password on droids2 Android App
In this writeup, I will walk you through the steps I took to solve the droids2 challenge from PicoCTF 2019, which involves Android reverse engineering. This challenge is similar to droids0 but has a little different step for showing the flag.
Tools that I used:
After downloading the APK, the screen is still same with droids0 and droids1 but this time the hint is “smali sounds like an ikea bookcase”. it might related to smali code when reversing android app.
From my understanding, smali code is an assembly language used for the Dalvik Virtual Machine (DVM) and this was overridden for the running of Android applications before the Android Run Time (ART). So when you decompile APK, the APK parses the jar and converts the Java bytecode to Smali, which is the readable form of the compiled classes and methods.
Also when you decompile the APK using Apktool it will give you the smali code and usually the case where hacker needs to have the smali code is when the hacker needs to modify / patch the original APK.
Before going deep into the smali code and modify the droids2 APK I tried to import the APK first into JADX to have a quick check of the code first.
Because on the MainActivity is still same with the previous challenge (droids1), I navigate directly into the FlagstaffHill Class
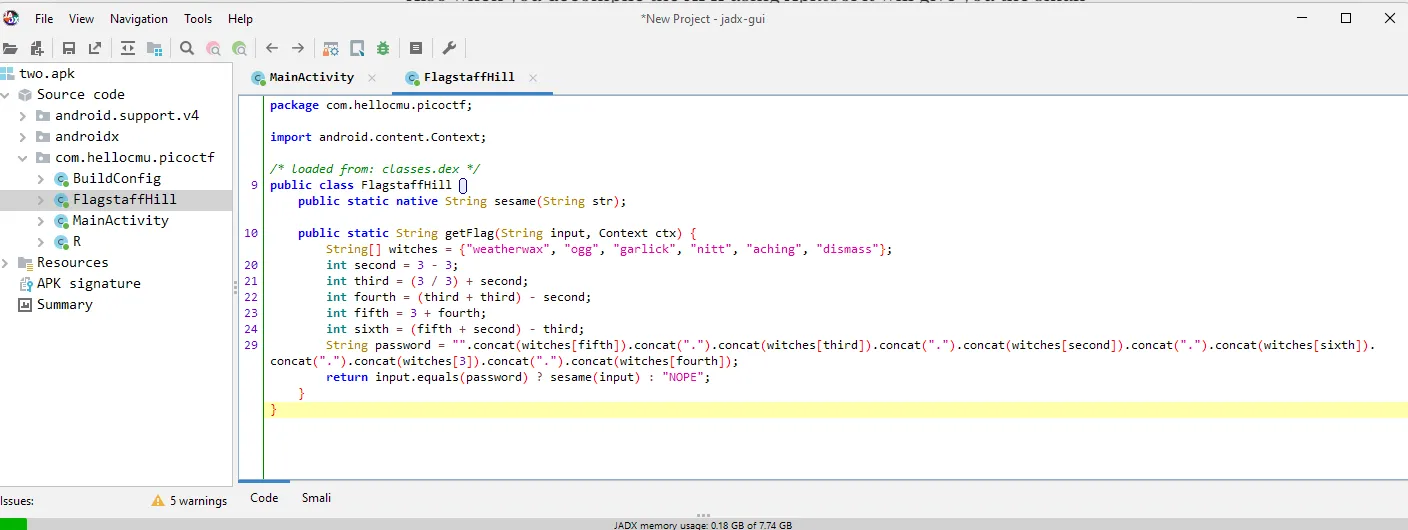
Turns out I might don’t need to solve this manually by checking the smali since JADX is doing a really good job for reversing the code and fortunately the code is quite straightforward. So Let’s just break down the code first
String[] witches = {"weatherwax", "ogg", "garlick", "nitt", "aching", "dismass"};
they have an Array of String called witches which contains some word
int second = 3 - 3;
int third = (3 / 3) + second;
int fourth = (third + third) - second;
int fifth = 3 + fourth;
int sixth = (fifth + second) - third;
after that, they also make several int variables that use some basic mathematic operation for the value
String password = "".concat(witches[fifth]).concat(".").concat(witches[third]).concat(".").concat(witches[second]).concat(".").concat(witches[sixth]).concat(".").concat(witches[3]).concat(".").concat(witches[fourth]);
then make a String variable called password, the value is combining the String with the value from array with index from the previous generated int variable and also adding “.” after each witches except the last witches. For Example
when calling witches[second] it will return weatherwax because on second value is 0 since 3 - 3 = 0 and witches with index 0 is weatherwax
String[] witches = {"weatherwax", "ogg", "garlick", "nitt", "aching", "dismass"};
int second = 3 – 3
print(witches[second]) // weatherwax
so in this case I just need to calculate and point the value for each witches called on the password with the index from the previous int variables and to make it easier I copy the code into Notepad make some changes and add some comments to note so my notepad looks like this.
public class FlagstaffHill {
public static native String sesame(String str);
public static String getFlag(String input, Context ctx) {
String[] witches = {"weatherwax", "ogg", "garlick", "nitt", "aching", "dismass"};
int second = 3 - 3; //0
int third = (3 / 3) + second; //1
int fourth = (third + third) - second; //2
int fifth = 3 + fourth; //5
int sixth = (fifth + second) - third; //4
String password = "".
concat(witches[fifth]). //dismass.
concat(".").concat(witches[third]) //ogg.
.concat(".").concat(witches[second]).concat(".") //weatherwax.
.concat(witches[sixth]).concat(".") //aching.
.concat(witches[3]).concat("."). //nitt.
concat(witches[fourth]); //garlick
return input.equals(password) ? sesame(input) : "NOPE";
}
}
so the result is this
dismass.ogg.weatherwax.aching.nitt.garlick
after getting the result, I just need to submit it to the EditText and get the Flag
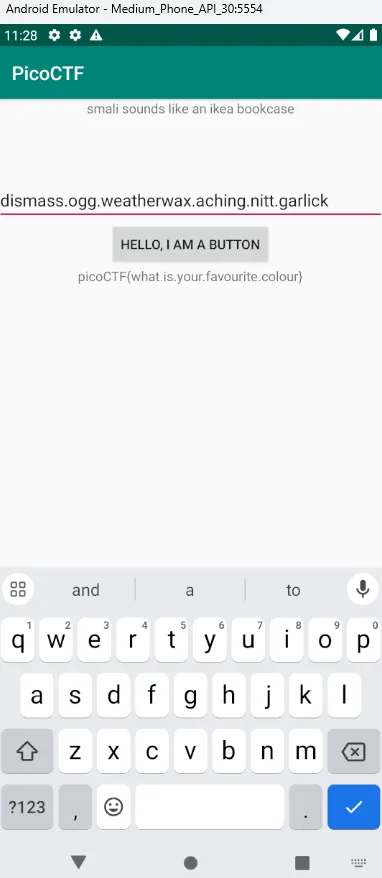
finally, here comes the flag
picoCTF{what.is.your.favourite.colour}
Reference:
OWASP Mobile - M7: Insufficient Binary Protection
